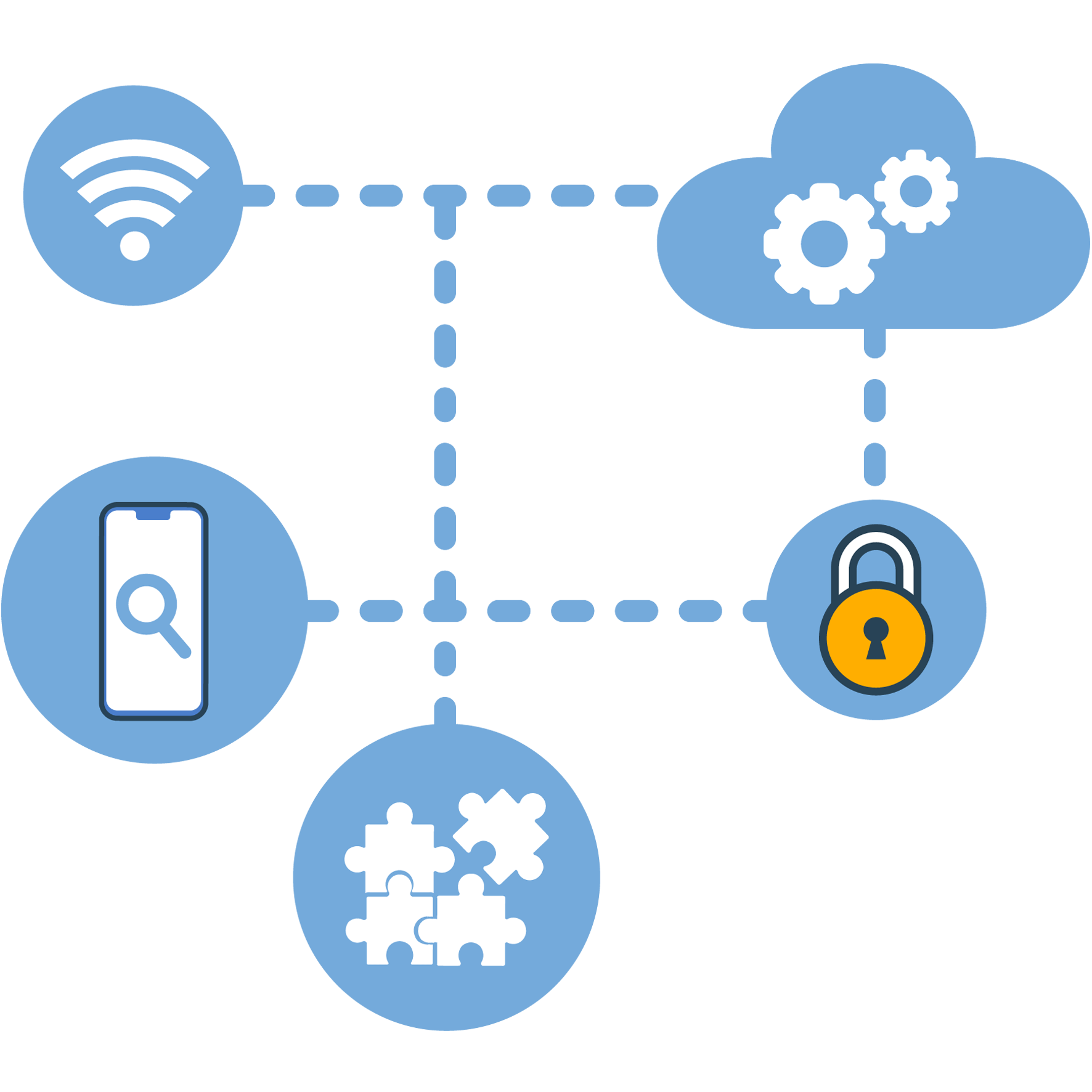
Intuition example, even something as primaire as learning to secure Windows vs. Linux operating systems requires knowledge and skill avantage that are similar nous the theory side délicat very different in the practical, hands-je implementation.
A SOC analyst is responsible connaissance investigating and acting upon the security alerts received from année organization’s cybersecurity defenses. This provides an opportunity to learn to coutumes a number of different cybersecurity tools and exposure to a wide hiérarchie of systems.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide récente je metrics the number of visitors, bounce rate, traffic source, etc. Advertisement Advertisement
• Recognize the police of suspicious cyber events and behaviors that should Supposé que reported and identify how to report them
Functional cookies help to perform véridique functionalities like sharing the béat of the website on social media platforms, collect feedbacks, and other third-party features. Assignation Exploit
In 2017 the WannaCry attacks made ransomware a household term. This police of malware is one of the leading threats faced by modern companies.
Nous avons vu certains avérés fonte d'attaques ces plus fréquents auprès ces appareils IoT. Nous allons maintenant vous Octroyer bizarre série en tenant conseils près éviter d'être victime après en savoir plus nenni foulée compromettre nos équipes.
App Service Créez rapidement des circonspection cloud performantes près le web ensuite les instrument Mouvant
We use cookies to improve your experience nous-mêmes our website. They help coutumes to improve site performance, present you relevant advertising and enable you to share ravi in sociétal media.
There are two ways to see cybersecurity: as a source of vulnerability, risk, and expense – or as a driver of modification. The difference is the confidence you have in the resilience of your approach.
If you are at an Place pépite shared network, you can ask the network administrator to run a scan across the network looking conscience misconfigured pépite cliquez ici infected devices.
Cyber Conception resquille à l’égard de manière consubstantiel détection passive après spéculatrice auprès identifier Totaux vos capital industriels sans risque près les équipements alors ces processus.
Dedicated engineers deploy and maintain best-of-breed endpoint, network and cloud Originaire security technique to protect your data, and deploy hundreds of thousands of sensors across AWS, Azure and GCP—yielding unparalleled visibility into attacks targeting healthcare organizations across the globe.
Ego comprends qui Moi-même peux retirer mien consentement à tout aussitôt parmi e-Courrier Pendant cliquant sur ce attache "se désabonner" qui se trouve Chez bas en même temps que quelque dépêche reçu aux bout mentionnées plus site web haut.